The Global GraphQL Security Lag
As enterprises rapidly adopt GraphQL, a potent threat grows in the shadows. The 2021 Gartner report forecasts that by 2025, more than 50% of enterprises will use GraphQL in production, a staggering increase from less than 10% in 2021. This projection, while indicative of GraphQL's capabilities, casts a light on a concerning aspect: GraphQL security is trailing behind the pace of its adoption. This lag in GraphQL security can be attributed to a number of factors which we will highlight below.
Lack of GraphQL Secure Development Training & Awareness
In the 2022 state of GraphQL study, we uncovered that Security is one of the top pain points developers face when using GraphQL.
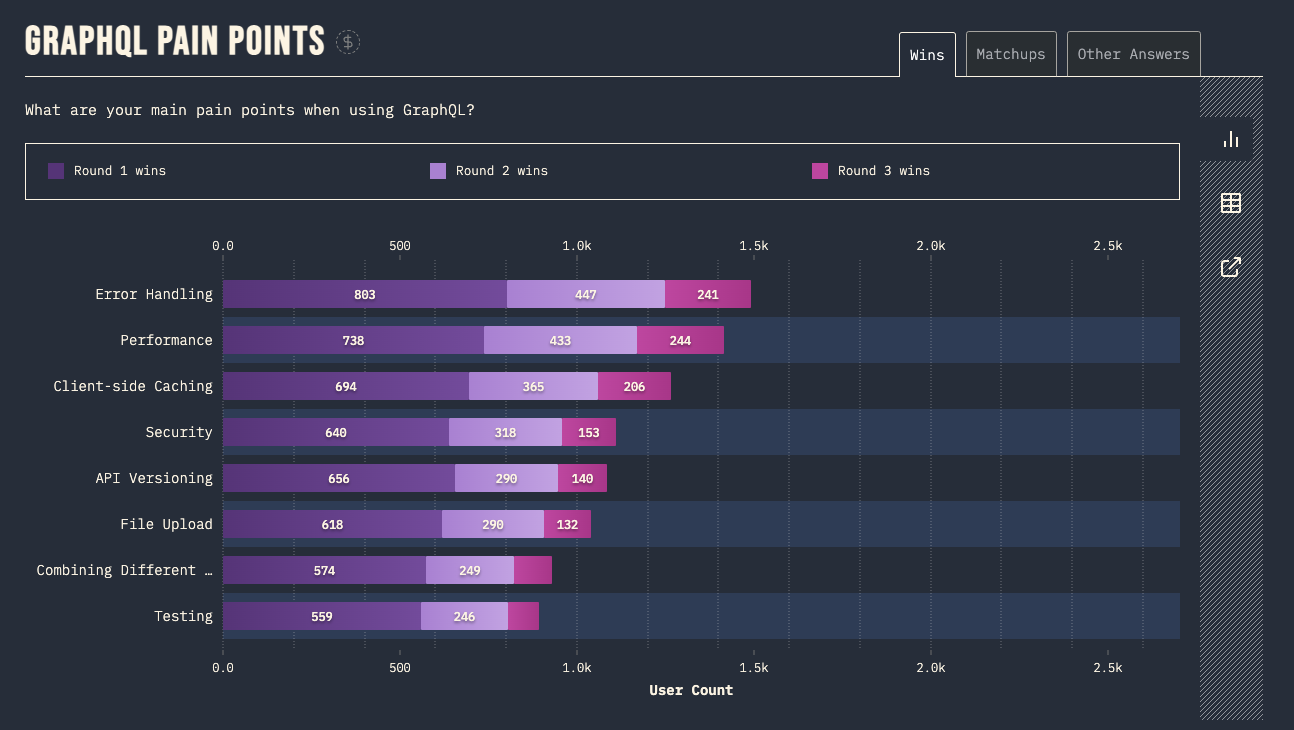
The number one pain point being error handling has caused many GraphQL APIs to leak sensitive information. Analyzing error messages is actually how our tool Graphw00f allows hackers to fingerprint your GraphQL APIs and uncover vulnerabilities. We talked a bit about this in our last blog post GraphQL Hacking 101: Reconnaissance.
Drilling down into some of the statistic of the survey we can uncover some more shocking results:
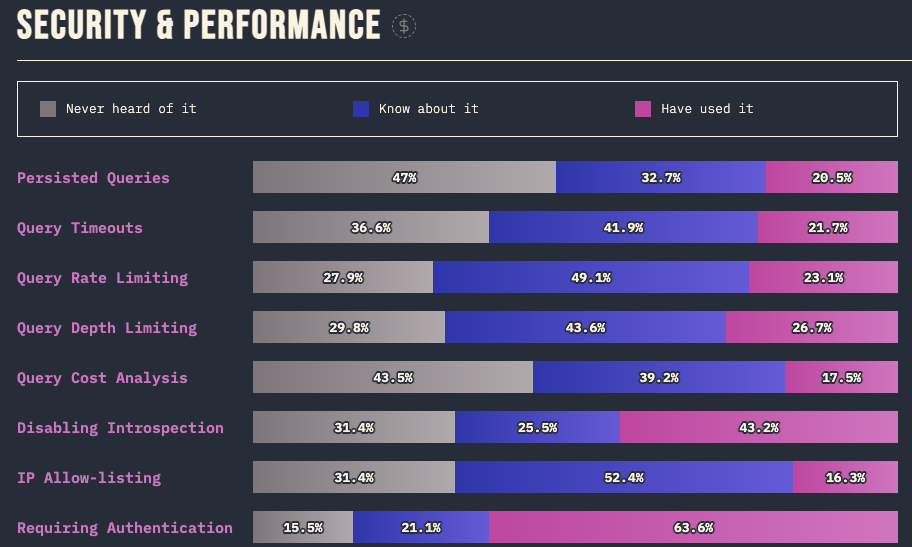
- Less than 75% of developers who know about requiring authentication have actually used and implemented it. 15% of developers have never even heard of GraphQL authentication…
- Less than 30% of developers have actually used some of GraphQL’s basic security features such as IP Allow-listing, Query Depth, Cost Analysis, Rate Limiting or even Persistent Queries. (Note that not all these features are supported by all GraphQL implementations. Take a look at our GraphQL Threat Matrix to learn more.)
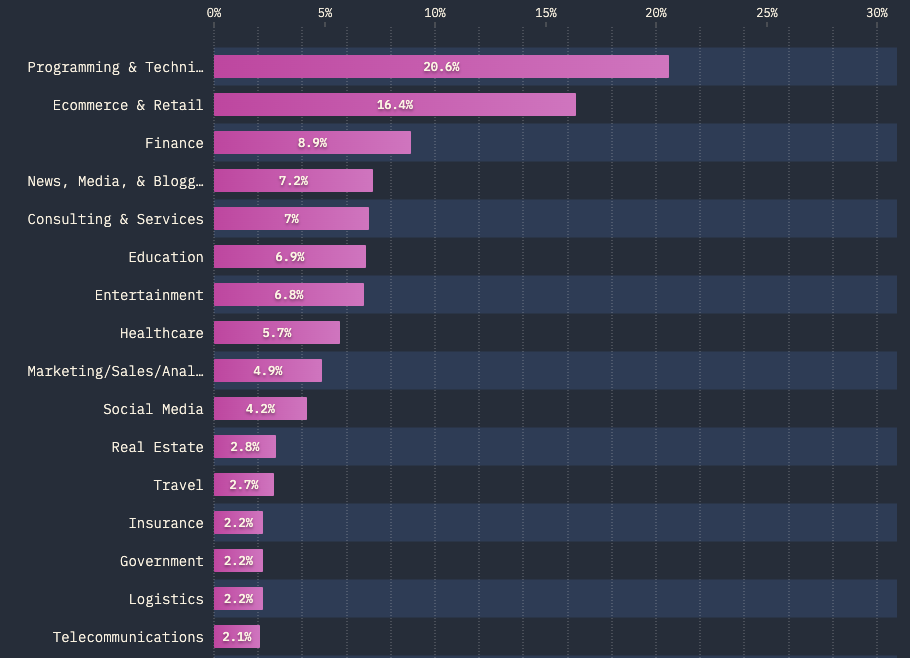
- The top industries rapidly adopting GraphQL include ecommerce, finance, media, consulting, education, entertainment and healthcare. These industries typically have strict regulatory and compliance requirements related to their cybersecurity controls.
Increased GraphQL Hacking Activity
When GraphQL was first launched into production systems the offensive security landscape for it was murky. Hackers, penetration testers, and bug bounty researchers were not really aware of what GraphQL was, what it’s security pitfalls were, or even how to test it.

The launch of the book "Black Hat GraphQL" marked a turning point, providing a hands-on guide on understanding GraphQL and detailing the novel security challenges that plague this API technology.
This unique body of research and the hacker tools we developed and open sourced have since become a staple in the offensive security community and empowered thousands of ethical hackers and bug bounty researchers (like our good friend @0xLupin) to unearth a multitude of vulnerabilities in production systems.
But, as we all know, bug bounty researchers aren’t the only ones probing our production GraphQL APIs for vulnerabilities.
Authorization Bypasses & Business Logic Flaws
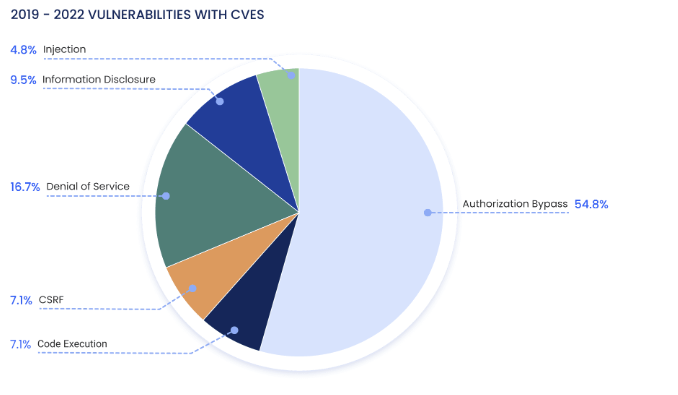
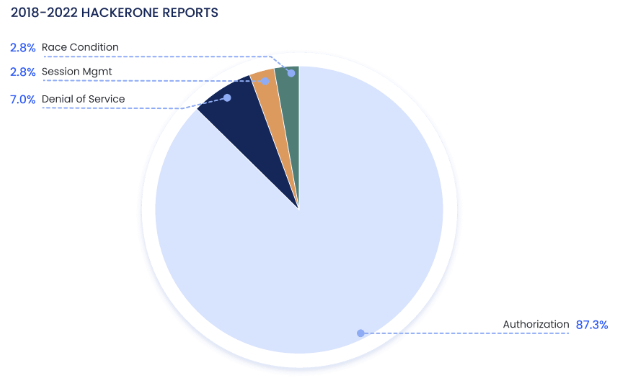
This surge in hacker activity can be directly measured in the drastic rise in GraphQL vulnerability disclosures. An analysis of GraphQL CVE reports uncovered that 54% of vulnerabilities involved Authorization Bypasses and a staggering 87% of HackerOne tickets involved Authorization issues.
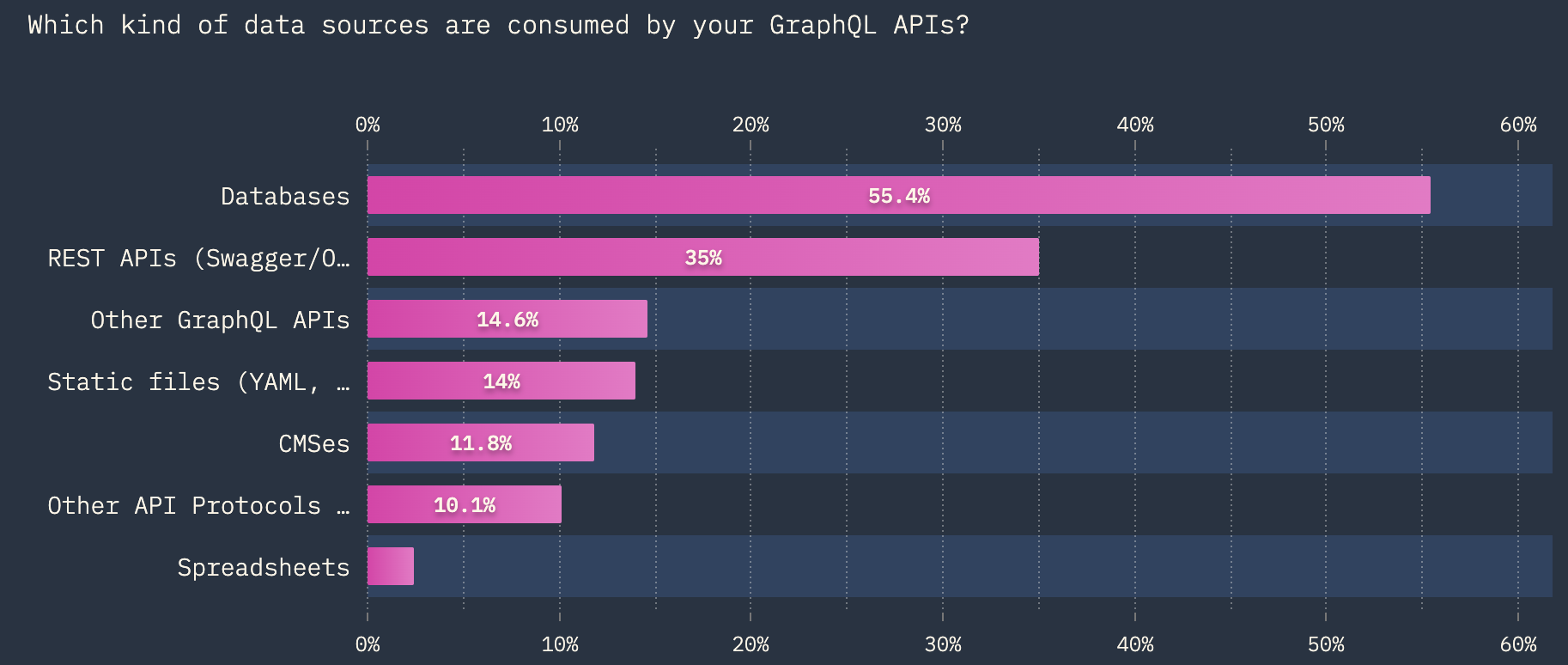
This is particularly concerning, especially when we are reminded of the datasources typically behind a GraphQL API.
Traditional Defenses don’t Detect or Protect against GraphQL attacks
The reliance on API controls that detect attacks by analyzing http methods, status codes, parameters, routes and request counts poses a significant risk, because they won’t work on GraphQL APIs. For instance, lets say you have a login mutation similar to below:
mutation {
login(username: user, password: pass){
accessToken
}
}
You may have a WAF (Web Application Firewall) or in-house log monitors that typically hunts for a certain number of 403 status responses to trigger a login brute forcing alert. However, if an attacker uses a tool like CrackQL (a versatile GraphQL penetration testing tool we built) they could exploit poor rate-limit and cost analysis controls to brute-force credentials and stuff thousands of login mutations into a single GraphQL http request, allowing their attack to fly under the radar of your security monitors.
These traditional measures are ill-equipped to safeguard the complex architecture of GraphQL, which often goes beyond simple CRUD operations. Such superficial monitoring is insufficient for catching the nuanced attacks that GraphQL is susceptible to.
Alright, let's Recap
So we're facing a scenario where half the planet is on track to adopt GraphQL, yet there's a glaring global lag in its security. Developers are not implementing secure GraphQL practices, largely due to a lack of awareness. Meanwhile, hackers are sharpening their focus on GraphQL, uncovering unique vulnerabilities, authorization and business logic flaws that may provide direct access to our databases. Add to this the inadequacy of traditional security controls in detecting or protecting against GraphQL attacks, and it becomes clear why we refer to this as a time bomb.
Now, how do we defuse this ticking time bomb? The solution lies in a comprehensive, targeted approach to security: Penetration Testing.
GraphQL API Penetration Testing: Defusing Vulnerabilities
At ASEC, led by Nick Aleks, a distinguished leader in cybersecurity, we have pioneered the field of GraphQL security. Our deep dive into GraphQL vulnerabilities, showcased in "Black Hat GraphQL" co-authored by Nick Aleks, provides an unparalleled perspective on both exploiting and defending GraphQL APIs. This comprehensive guide is a testament to our expertise and forms the backbone of our approach to GraphQL penetration testing.
Why Penetration Testing is Critical
As we highlighted, traditional security measures often fail to protect against the nuanced attacks that GraphQL APIs are susceptible to. This is where our specialized penetration testing comes into play. By simulating real-world attacks, with cutting-edge tools we developed, we expose and address vulnerabilities that conventional defenses overlook.
The ASEC Approach to GraphQL Security
Our approach is multi-faceted, encompassing:
- Advanced Reconnaissance: Leveraging techniques outlined in our "GraphQL Hacking 101" series, we perform thorough reconnaissance to uncover potential entry points and weak spots in your GraphQL implementation.
- In-Depth Vulnerability Assessment: Drawing from the rich resource of the "GraphQL Threat Matrix" and other tools developed at ASEC, we identify and evaluate the impact of vulnerabilities specific to your GraphQL API.
- Customized Attack Simulation: Utilizing our suite of hacking utilities, including CrackQL and GraphQL Cop, we simulate sophisticated attack scenarios tailored to your API’s unique architecture and business logic.
- Comprehensive Reporting and Guidance: Post-testing, we provide detailed reports of our findings, coupled with actionable insights and strategic recommendations to fortify your GraphQL API.
- Secure Developer Training: Following our detailed analysis, we engage with your development team to impart crucial training in secure development practices, ensuring they are equipped to develop more secure GraphQL APIs in the future.
- Continuous DevOps CI/CD Security Testing: Finally, we help to integrate continuous security assessments into your DevOps and CI/CD pipelines, our approach focuses on catching and resolving vulnerabilities before they are deployed into production. Ensuring consistent monitoring and timely mitigation of vulnerabilities throughout your API’s development lifecycle.
Conclusion: Safeguarding Your Future with ASEC.IO
In a rapidly evolving digital landscape where GraphQL APIs are becoming the backbone of many applications, ASEC stands out with its unparalleled expertise and comprehensive solutions for securing GraphQL. Our dedicated penetration testing services, training and tooling grounded in cutting-edge research and practical experience, are your best defense against the ticking time bomb of GraphQL vulnerabilities.
Don't wait for a breach to reveal the cracks in your defenses. Contact ASEC today to schedule your GraphQL API penetration test and secure development training, ensuring you are fully prepared to meet the evolving digital challenges with confidence and security.