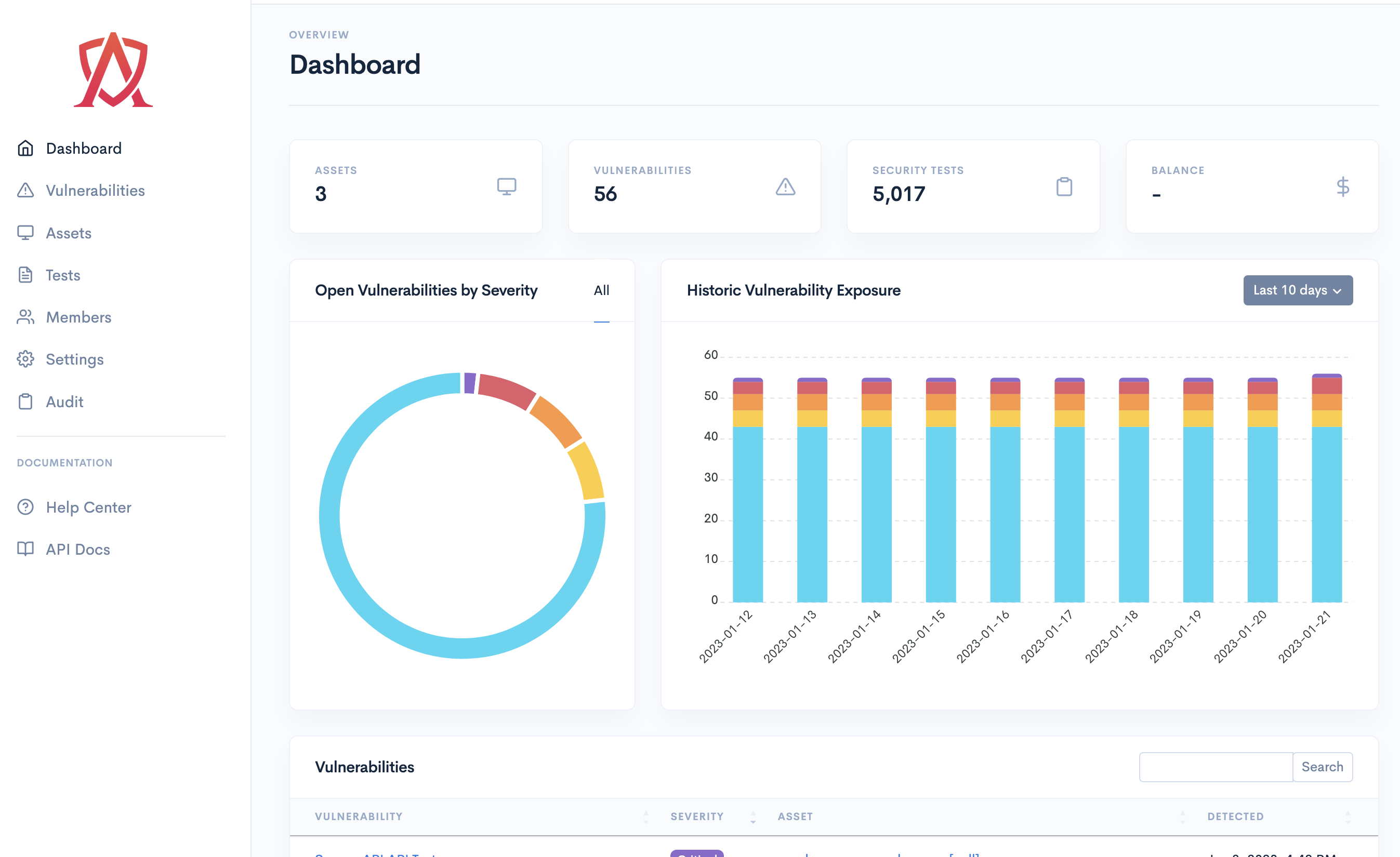
Continuous Security Testing
Bad actors are constantly testing your perimeter and attack surface. Why not do the same? Emulate the exact same attacks adversaries are executing against your systems and patch them before they are exploited.
Private nuclei cluster
Instant results
Scheduled testing
REST API