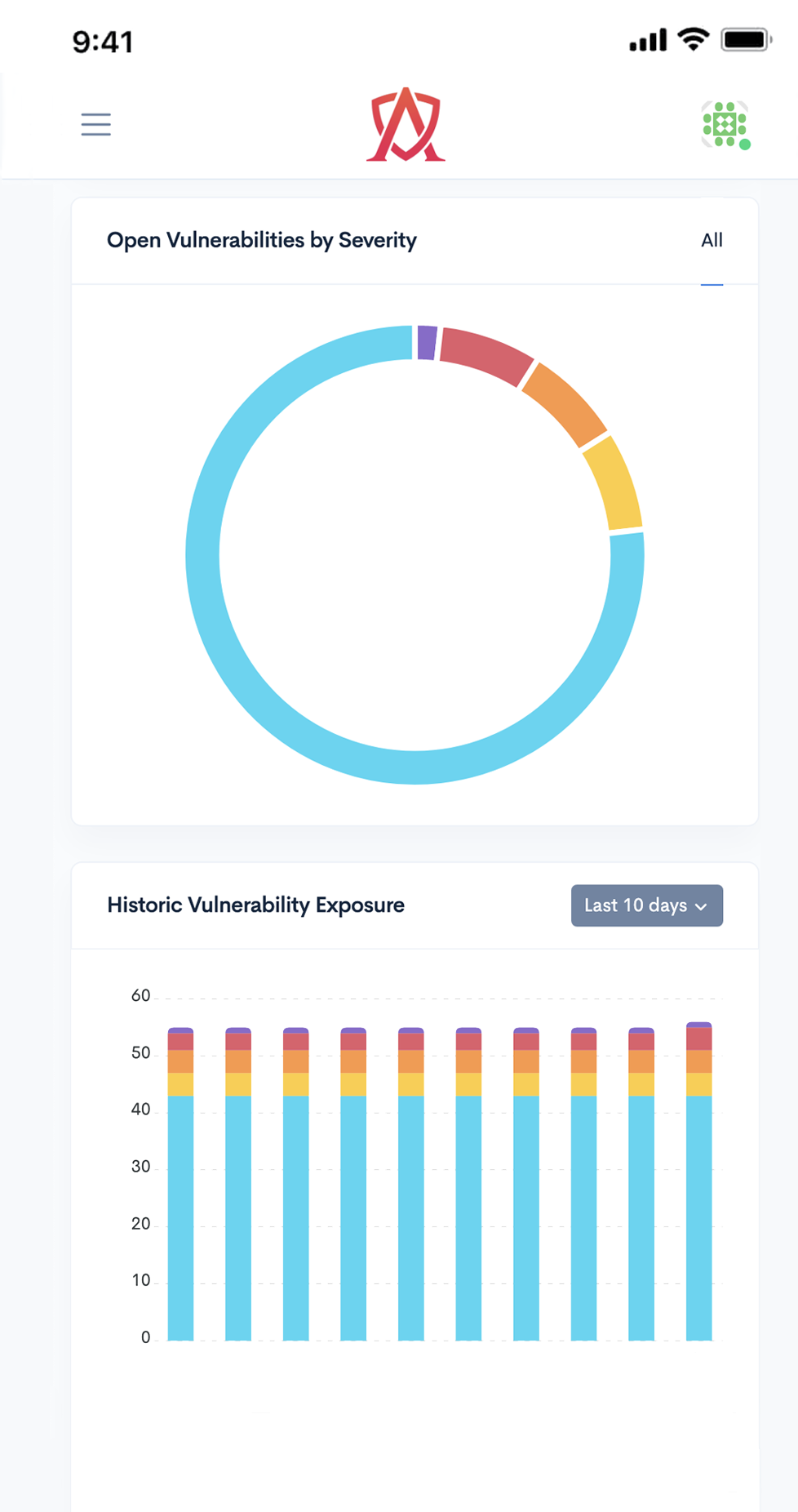
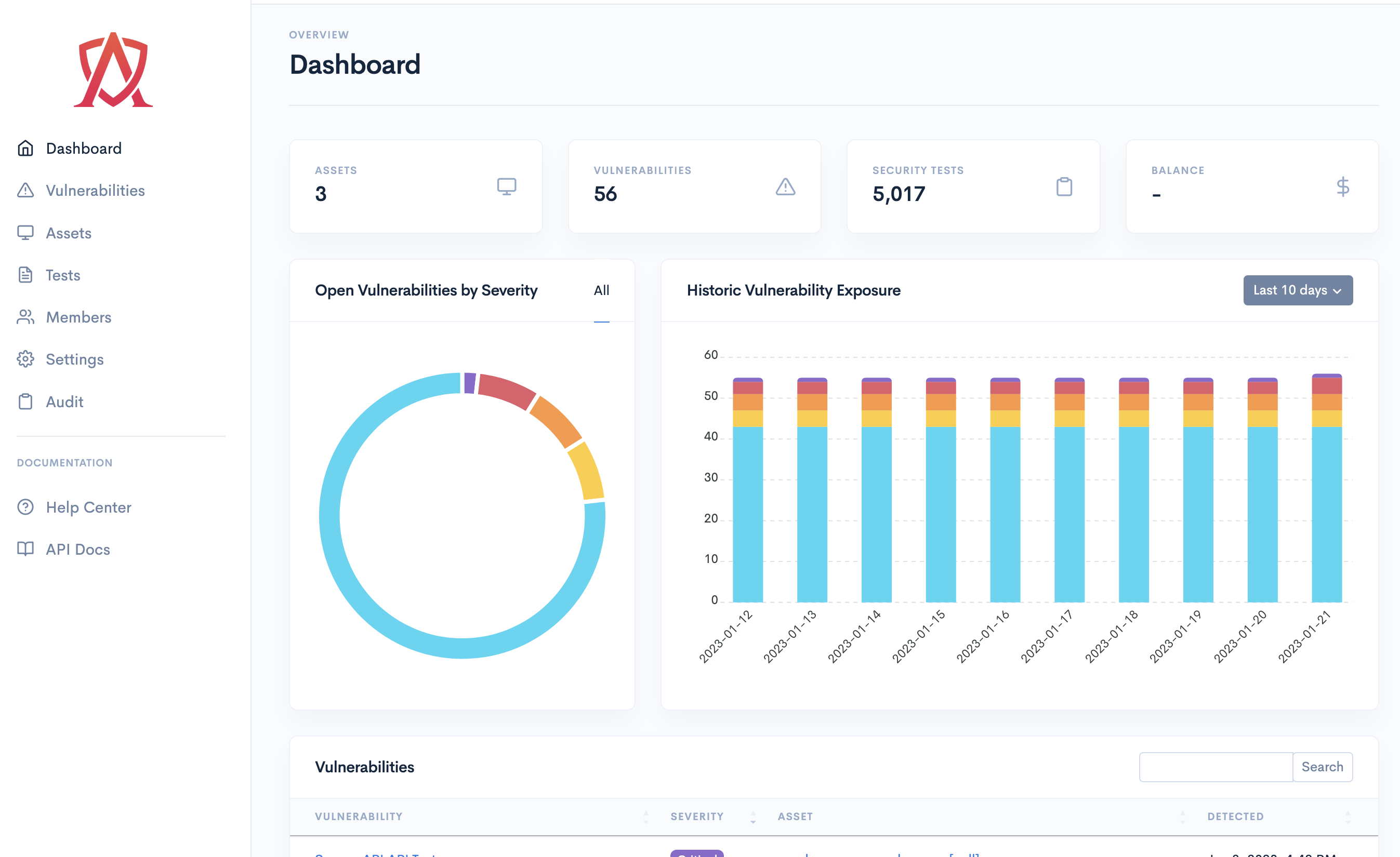
A Cyber Security Maturity Assessment is a gap analysis and risk assessment that utilizes cybersecurity best practices and recognized cyber frameworks to answer these questions surrounding your existing security program.
Assessing the maturity of a security program against the National Institute of Standards (NIST) Cyber Security Framework (CSF) gives an organization context into how balanced their security investments are across identifying, preventing, detecting, responding and recovery to cyber threats.
ASEC evaluates the maturity of an organization’s security program against NIST CSF using a series of interviews, evidence collection and analysis of working controls across people, processes and technology. We then execute lightweight tests to ensure controls are working reliably in accordance with how they are documented and communicated.
Indentify Maturity
The Identify Function assists in developing an organizational understanding to managing cybersecurity risk to systems, people, assets, data, and capabilities. Understanding the business context, the resources that support critical functions, and the related cybersecurity risks enables an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs.
-
Asset Management
-
Business Environment
-
Governance
-
Risk Assessment
-
Risk Management Strategy
Protect Maturity
The Protect Function outlines appropriate safeguards to ensure delivery of critical infrastructure services. The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event.
-
Access Control
-
Awareness and Training
-
Data Security
-
Information Protection Processes and Procedures
-
Maintenance
-
Protective Technology
Detect Maturity
The Detect Function defines the appropriate activities to identify the occurrence of a cybersecurity event. The Detect Function enables timely discovery of cybersecurity events.
-
Anomalies and Events
-
Security Continuous Monitoring
-
Detection Processes
Respond Maturity
The Respond Function includes appropriate activities to take action regarding a detected cybersecurity incident. The Respond Function supports the ability to contain the impact of a potential cybersecurity incident.
-
Response Planning
-
Communications
-
Analysis
-
Mitigation
-
Improvement
Recover Maturity
The Recover Function identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident. The Recover Function supports timely recovery to normal operations to reduce the impact from a cybersecurity incident.
-
Recovery Planning
-
Communications
-
Improvements